Load balancing Microsoft Exchange
Benefits of load balancing Microsoft Exchange
Load balancing Microsoft Exchange is essential for:
- High Availability (HA): Load balancing is critical for maintaining continuous access to email, calendars, and contacts. The load balancer constantly monitors the health of all Exchange servers. If one server fails or a specific service on a server stops responding (e.g., Outlook Web App), the load balancer automatically stops sending new traffic to the unhealthy server and redirects all client requests to the remaining healthy servers. This seamless failover process ensures that users remain connected to the Exchange environment, significantly reducing downtime and providing a resilient service. It also allows administrators to take an Exchange server offline for maintenance, patching, or upgrades without interrupting service for users. The load balancer simply routes traffic away from the server under maintenance.
- Scalability: Load balancing allows businesses to handle a growing user base or peak traffic loads effectively by enabling horizontal scaling. It intelligently distributes incoming client connections across a pool of multiple Exchange servers. This prevents any single server from becoming overloaded, ensuring smooth operation for all users. When the organization grows, it can easily add new Exchange servers to the backend pool. The load balancer automatically incorporates the new server and begins distributing traffic to it, instantly increasing the environment’s total capacity.
- Optimal performance: By intelligently sharing the workload, load balancing ensures users get the best possible experience and that your server resources are used efficiently. By sending traffic to the least busy or most efficient server, the load balancer minimizes latency and ensures faster response times for users accessing their mailboxes. Various load balancing algorithms (like Least Connection or Weighted Round Robin) ensure that the processing load is evenly spread across all available resources, optimizing the utilization of your server infrastructure. This prevents resource saturation on a few servers while others sit idle.
Microsoft’s Enterprise solutions are at the heart of businesses everywhere. Loadbalancer.org is officially certified for all of Microsoft’s key applications which you can find here. More details on the Microsoft Exchange components, how it works, and prerequisites for load balancing can be found in our deployment guide, available to view below.
About Microsoft Exchange
Microsoft Exchange Server, the mainstay of Microsoft’s Unified Communications solution, has grown beyond being regarded as the standard in business email into a fully-fledged communications tool. Exchange 2019 is Microsoft’s latest enterprise-level messaging and collaboration server – its architecture is very similar to Exchange 2016.
Why Loadbalancer.org for Microsoft Exchange?
Loadbalancer’s intuitive Enterprise Application Delivery Controller (ADC) is also designed to save time and money with a clever, not complex, WebUI.
Easily configure, deploy, manage, and maintain our Enterprise load balancer, reducing complexity and the risk of human error. For a difference you can see in just minutes.
And with WAF and GSLB included straight out-of-the-box, there’s no hidden costs, so the prices you see on our website are fully transparent.
More on what’s possible with Loadbalancer.org.
How to load balance Microsoft Exchange
The load balancer can be deployed in 4 fundamental ways: Layer 4 DR mode, Layer 4 NAT mode, Layer 4 SNAT mode, and Layer 7 Reverse Proxy (Layer 7 SNAT mode).
For Microsoft Exchange, Layer 4 DR mode or Layer 7 Reverse Proxy mode are recommended.
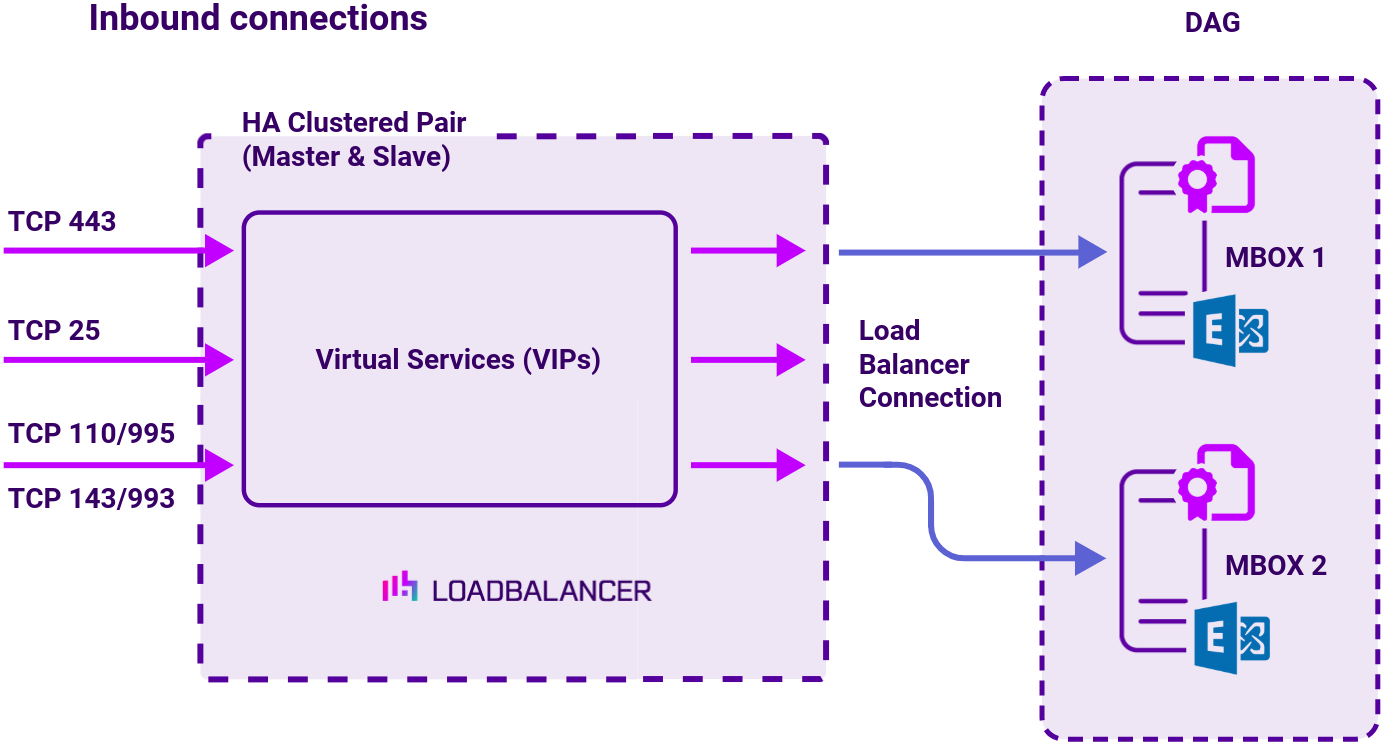
Virtual service (VIP) requirements
To provide load balancing and HA for Exchange 2019, the following VIPs are required:
- HTTPS (for all HTTPS based services)
- SMTP
Optionally, additional VIPs may be required as follows:
- HTTP (for redirecting to HTTPS, please refer to Using a Layer 4 Virtual Service for SMTP in the deployment guide for more details)
- IMAP4
- POP3
Load balancing deployment concept
To implement highly available and scalable deployments of Microsoft Exchange Server, Microsoft recommends using a load balancer to distribute the traffic among multiple Exchange servers. Both current and legacy versions of Exchange support load balancing, with a different approach and recommendations dependent on the version you are running.
The load balancer can be deployed in 4 fundamental ways: Layer 4 DR mode, Layer 4 NAT mode, Layer 4 SNAT mode and Layer 7 SNAT mode.
- For Exchange 2019, 2016 or 2010 we recommend using Layer 7 SNAT mode for simplicity
- For Exchange 2013, where possible we recommend Layer 4 Direct Routing (DR) mode
Exchange 2019, 2016 and 2013 protocol table
| Protocol | Role | Ports | Load balancing methods |
|---|---|---|---|
| TCP | CAS | 443 | Used for Outlook on the Web, AutoDiscovery, Web Services, ActiveSync, Outlook Anywhere, Offline Address Book, Exchange Administration Center). Layer 4 DR (Direct Routing – Ultra-fast, local server based load balancing) Layer 7 SNAT |
| TCP | CAS | 25 | Used for Inbound SMTP Layer 4 DR (Direct Routing – Ultra-fast, local server based load balancing) Layer 7 SNAT (Flexible, URL switching and cookie insertion capabilities) |
| TCP | CAS | 110,995,143,993 | Used for POP3 clients Used for IMAP4 clients Layer 4 DR (Direct Routing – Ultra-fast, local server based load balancing) Layer 7 SNAT (Flexible, URL switching and cookie insertion capabilities) |
Exchange 2010 protocol table
| Protocol | Role | Ports | Load balancing methods |
|---|---|---|---|
| TCP | CAS | 80 | Layer 7 SNAT |
| TCP | CAS | 443 | Layer 7 SNAT |
| TCP | HT | 25 | Used for the HT (Hub Transport) role Layer 4 DR (Direct Routing – Ultra-fast, local server based load balancing) Layer 4 NAT (Fast Load balancing throughput) Layer 7 SNAT (Flexible, URL switching and cookie insertion capabilities) |
| TCP | CAS | 110, 995, 143, 993, 135, 60201 | Used for POP3 clients Used for IMAP4 clients RPC endpoint mapper Static port for Exchange address book service Layer 7 SNAT |
About Layer 4 DR mode load balancing
One-arm direct routing (DR) mode is a very high performance solution that requires little change to your existing infrastructure.
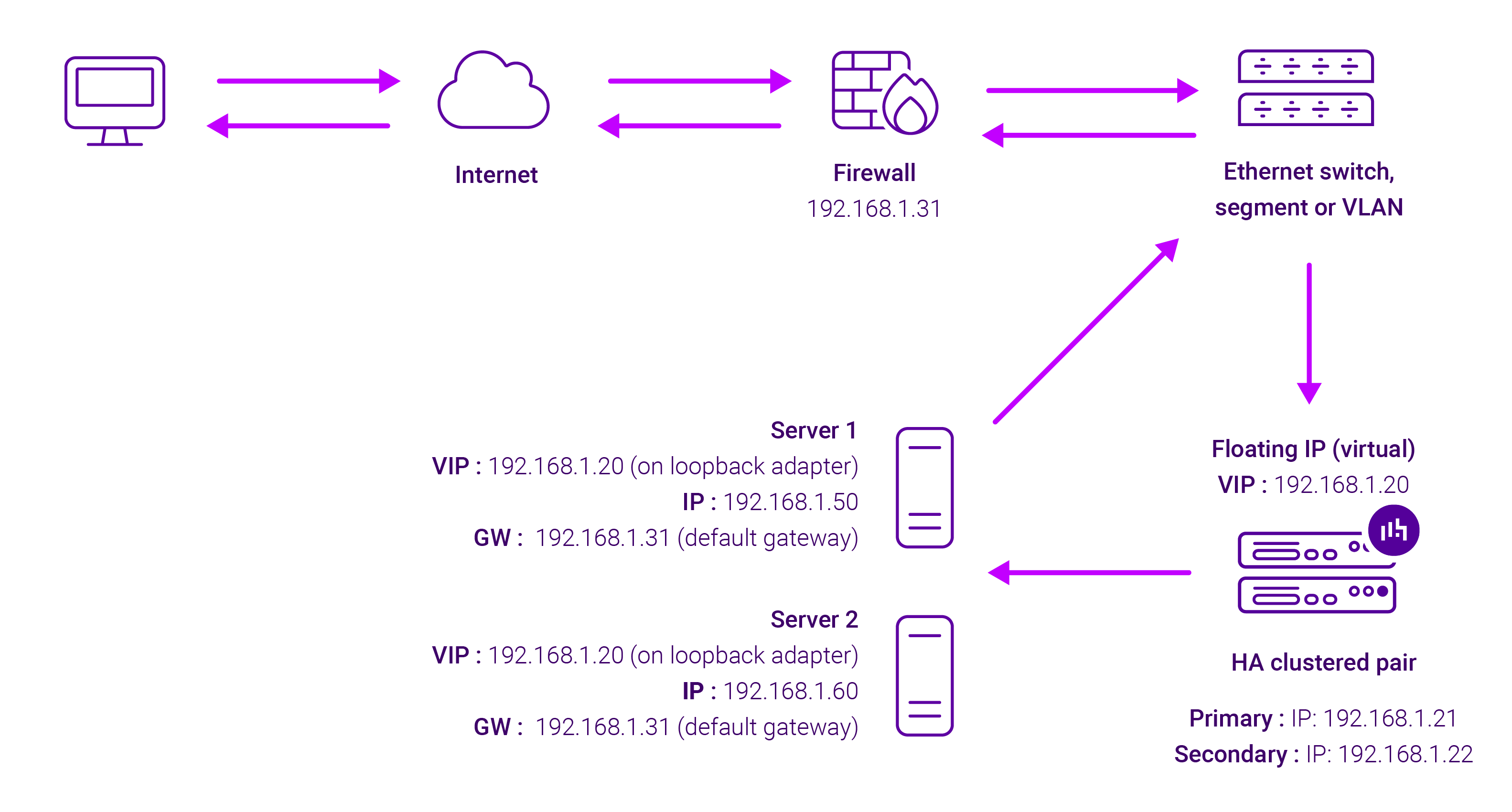
DR mode works by changing the destination MAC address of the incoming packet to match the selected Real Server on the fly which is very fast.
When the packet reaches the Real Server it expects the Real Server to own the Virtual Services IP address (VIP). This means that you need to ensure that the Real Server (and the load balanced application) respond to both the Real Server’s own IP address and the VIP.
The Real Servers should not respond to ARP requests for the VIP. Only the load balancer should do this. Configuring the Real Servers in this way is referred to as Solving the ARP problem.
On average, DR mode is 8 times quicker than NAT for HTTP, 50 times quicker for Terminal Services and much, much faster for streaming media or FTP.
The load balancer must have an Interface in the same subnet as the Real Servers to ensure Layer 2 connectivity required for DR mode to work.
The VIP can be brought up on the same subnet as the Real Servers, or on a different subnet provided that the load balancer has an interface in that subnet.
Port translation is not possible with DR mode, e.g. VIP:80 → RIP:8080 is not supported. DR mode is transparent, i.e. the Real Server will see the source IP address of the client.
About Layer 7 Reverse Proxy load balancing
Layer 7 Reverse Proxy uses a proxy (HAProxy) at the application layer. Inbound requests are terminated on the load balancer and HAProxy generates a new corresponding request to the chosen Real Server. As a result, Layer 7 is typically not as fast as the Layer 4 methods.
Layer 7 is typically chosen when enhanced options such as SSL termination, cookie based persistence, URL rewriting, header insertion/deletion etc. are required, or when the network topology prohibits the use of the Layer 4 methods.
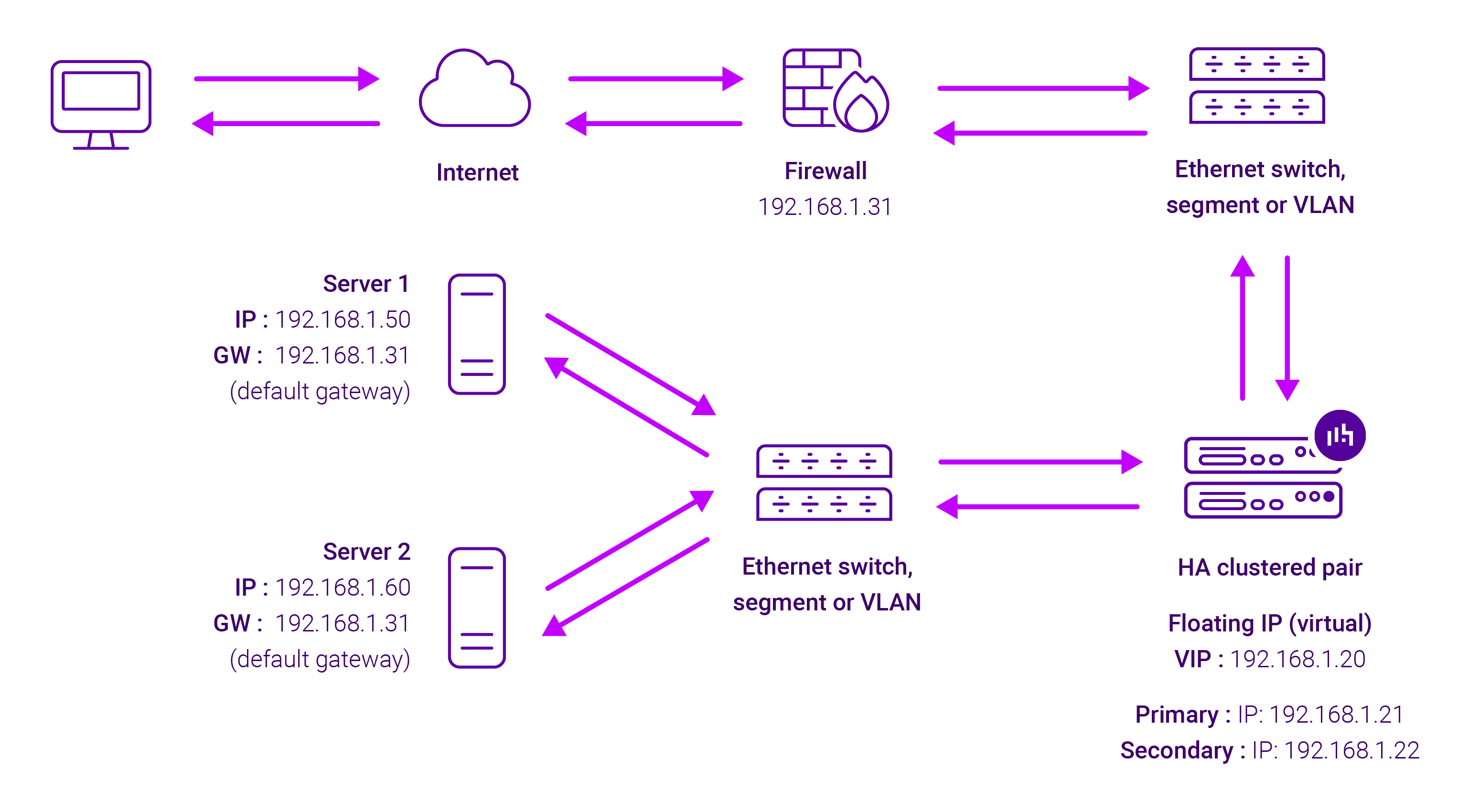
Because Layer 7 Reverse Proxy is a full proxy, any server in the cluster can be on any accessible subnet, including across the Internet or WAN.
Layer 7 Reverse Proxy is not transparent by default i.e. the Real Servers will not see the source IP address of the client, they will see the load balancer’s own IP address by default, or any other local appliance IP address if preferred (e.g. the VIP address). This can be configured per Layer 7 VIP.
If required, the load balancer can be configured to provide the actual client IP address to the Real Servers in two ways:
- Either by inserting a header that contains the client’s source IP address, or
- By modifying the Source Address field of the IP packets and replacing the IP address of the load balancer with the IP address of the client.
Layer 7 Reverse Proxy mode can be deployed using either a one-arm or two-arm configuration. For two-arm deployments, eth0 is normally used for the internal network and eth1 is used for the external network, although this is not mandatory.
No mode-specific configuration changes to the load balanced Real Servers are required.
Port translation is possible with Layer 7 Reverse Proxy e.g. VIP:80 → RIP:8080 is supported. You should not use the same RIP:PORT combination for Layer 7 Reverse Proxy VIPs and Layer 4 SNAT mode VIPs because the required firewall rules conflict.


















